Setup DUO 2FA with SonicWall SSL VPN
In this blog, I’ll detail how to integrate DUO’s Two Factor Authentication service for use with SonicWall’s NetExtender SSL VPN client. In the configuration I outline here, I will be using Active Directory integration for user authentication. I’m also assuming that you already have a working SSL VPN setup on your SonicWall and are just integrating the DUO 2FA service. This will not work with the SonicWall Global VPN Client.
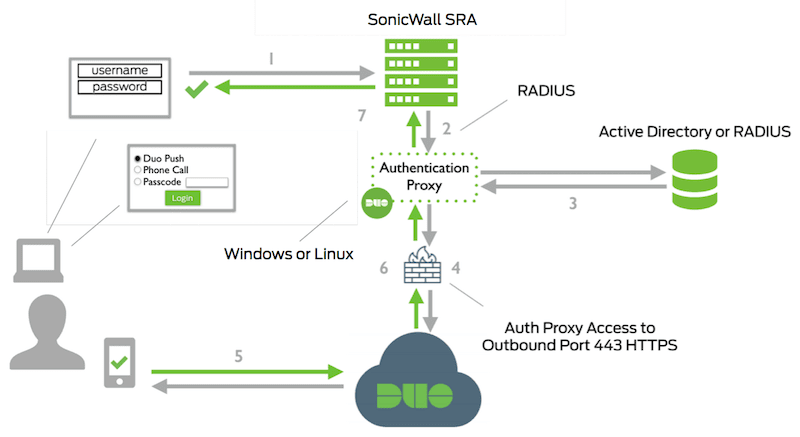
Here is a basic workflow diagram showing how the VPN authentication and RADIUS 2FA push notifications work.
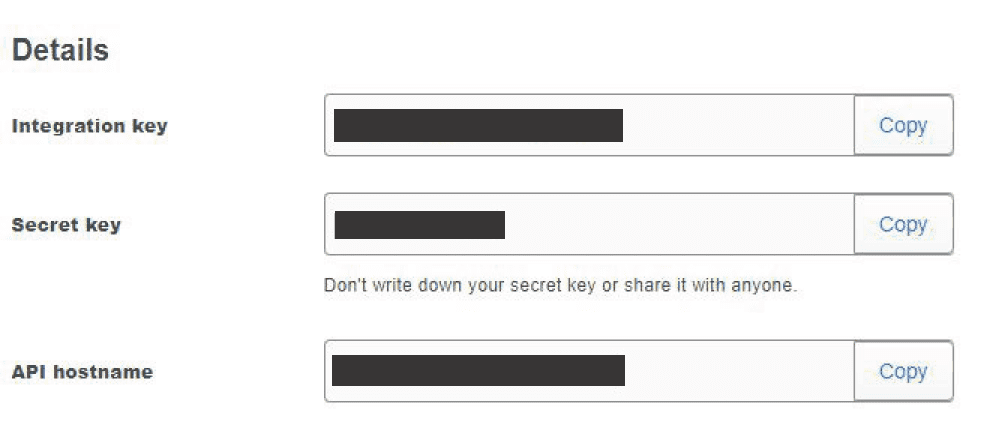
- First you’ll need to setup a DUO account. Once your account is created you’ll need to define an application (Your SSL VPN configuration) within the DUO dashboard that you will be protecting. Record your keys and keep in a safe place. Do not share these key with others. They will be used later on.

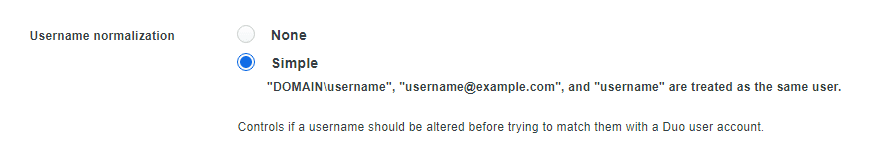
- Set your DUO application username setting to simple.

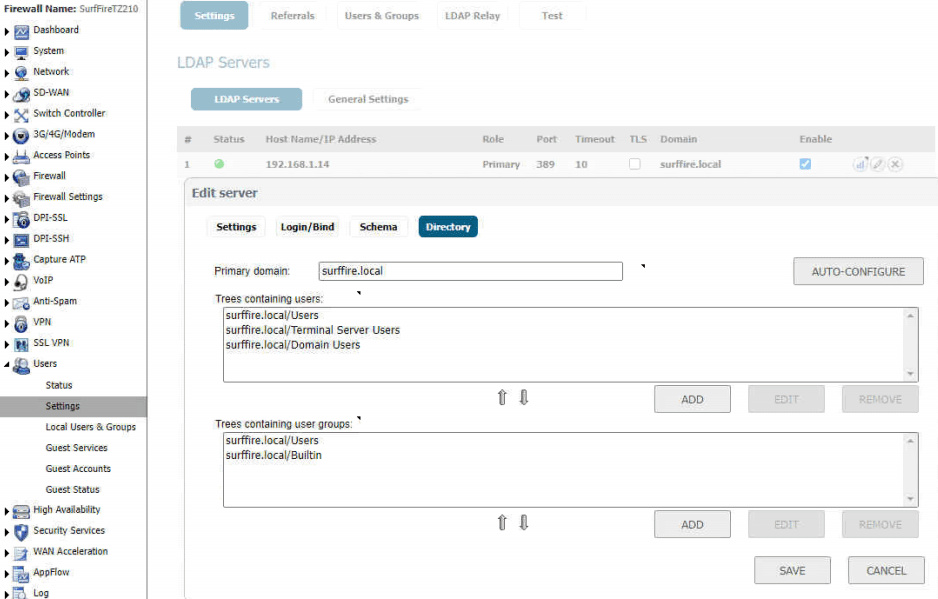
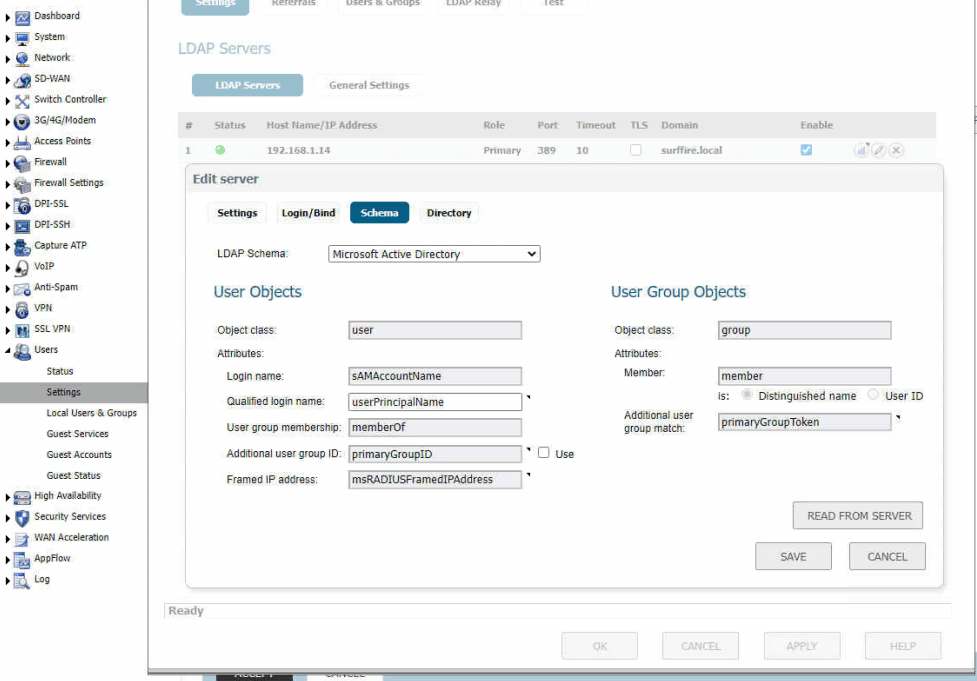
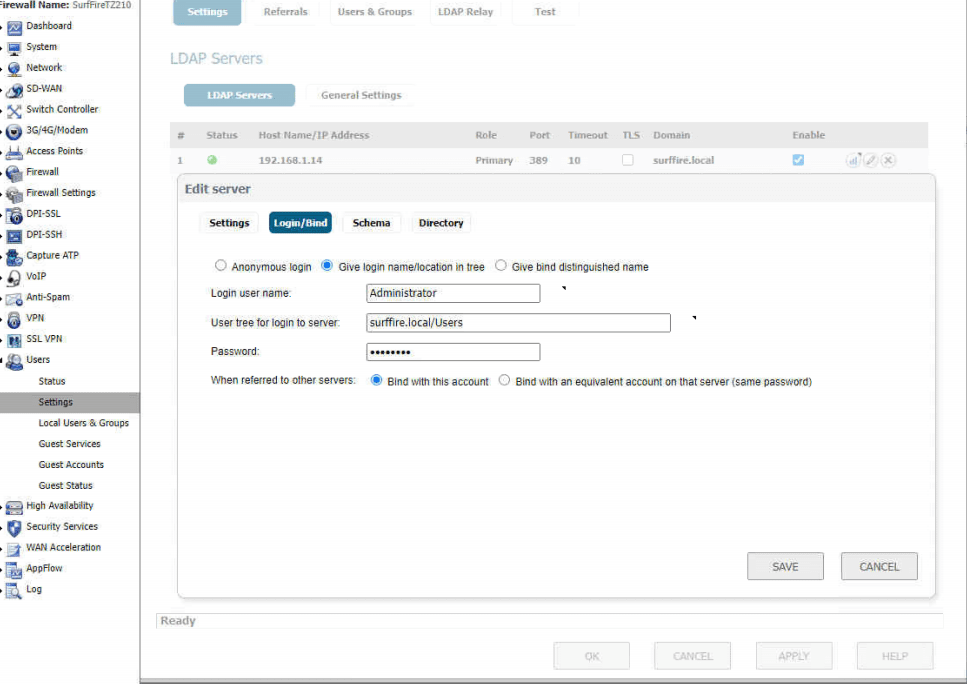
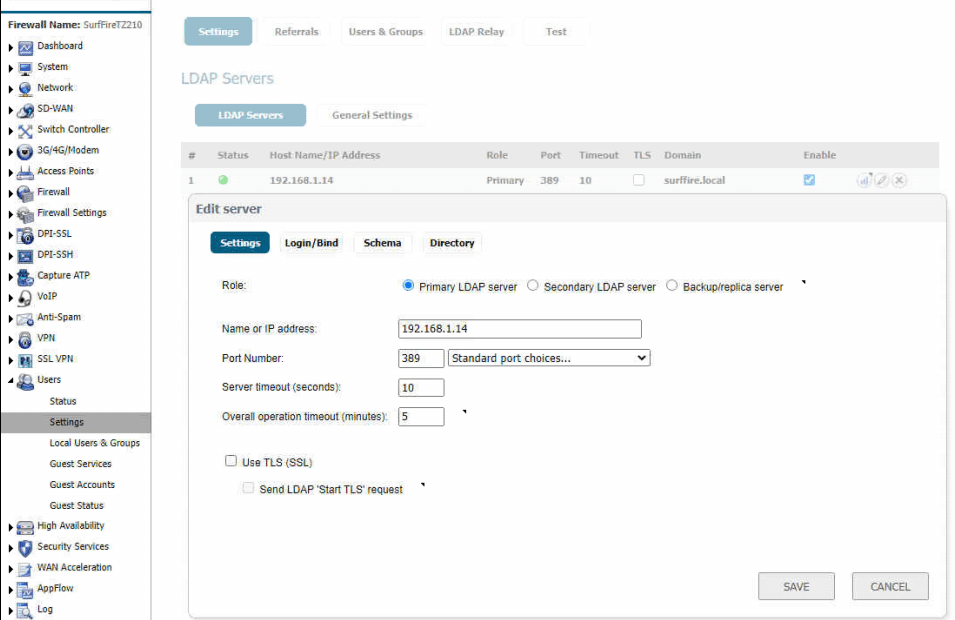
- Configure LDAP authentication in your SonicWall appliance. Here are some screen shots from my configuration.




- Install the Duo Authentication Proxy software on your AD Domain Controller. I used the following configuration in my proxy config file which utilizes LDAP authentication for the SSL VPN client and then DUO authentication for the 2FA. You will also need to create a read only AD service account for the LDAP authentication. That username and password will be specified below.
[ad_client]
host=IP_ADDRESS_OF_YOUR_DOMAIN_CONTROLLER
service_account_username=ENTER_YOUR_SEVICE_ACCOUNT_USER
service_account_password=ENTER_YOUR_SERVICE_ACCOUNT_PASSWORD
search_dn=DC=DOMAIN_NAME,DC=DOMAIN_SUFFIX
[radius_server_auto]
ikey=FROM_STEP_1
skey=FROM_STEP_1
api_host=FROM_STEP_1
radius_ip_1=SONICWALL_IP_ADDRESS
radius_secret_1=CREATE_A_RADIUS_SCRET_PASSWORD
failmode=safe
client=ad_client
port=18120
;pass_through_all=true
[main]
debug=true
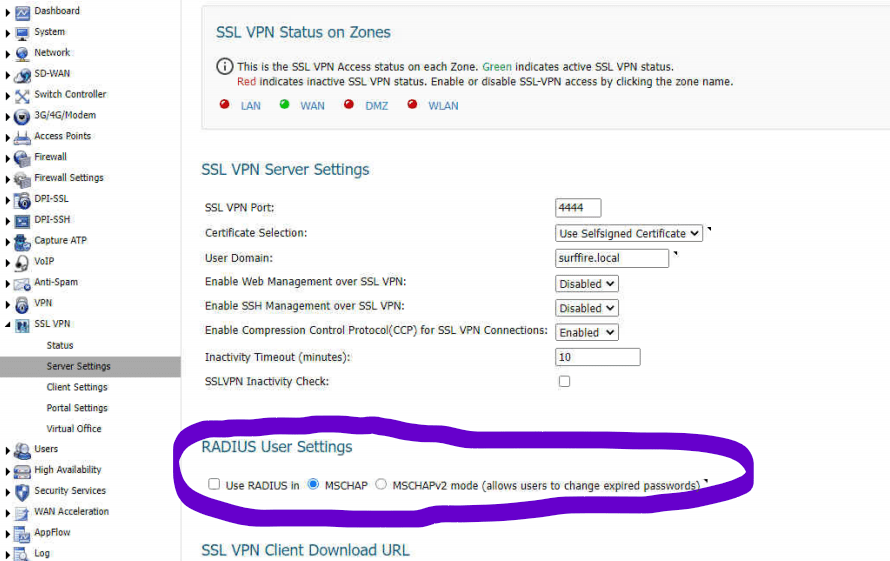
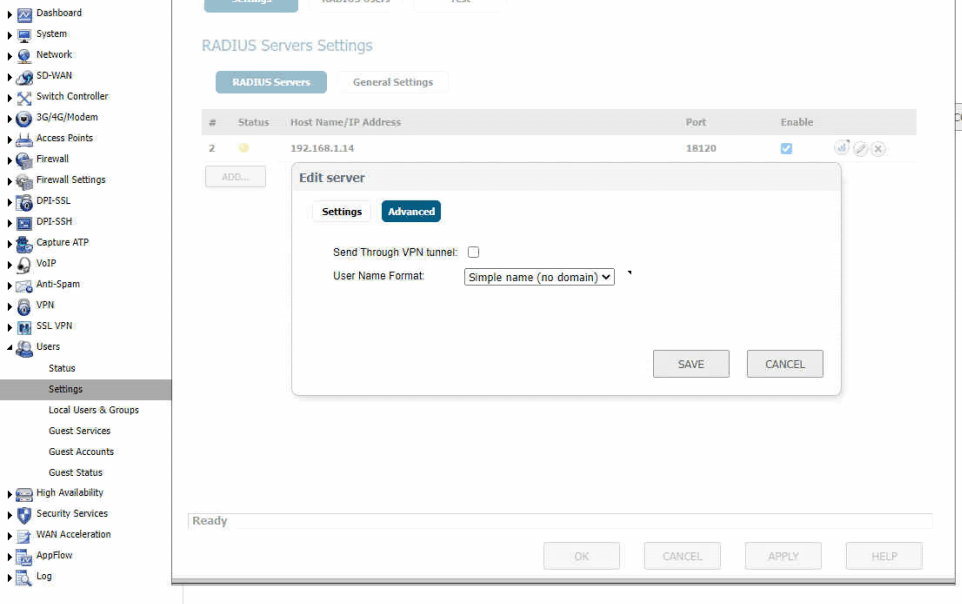
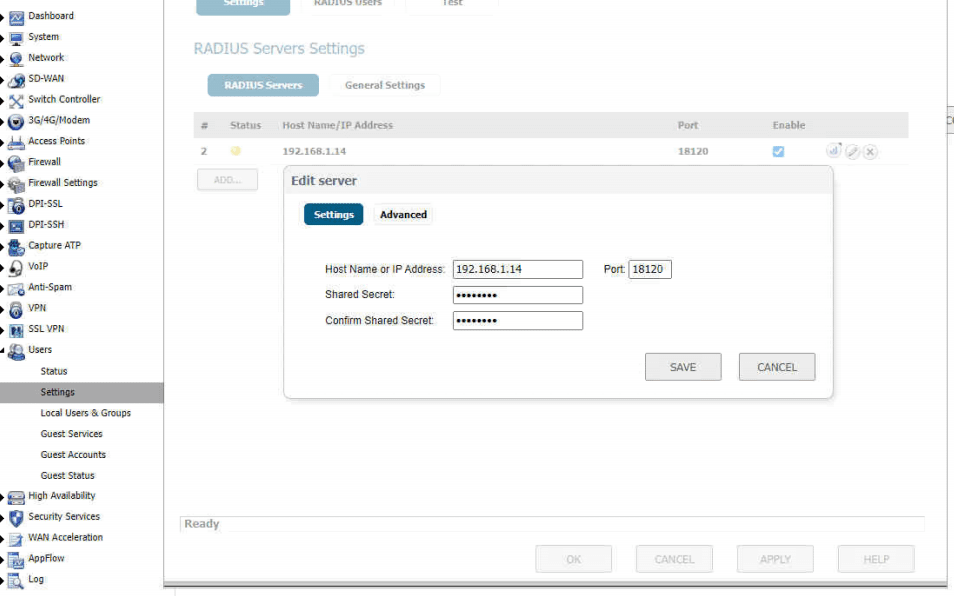
- Now you will need to configure the RADIUS authentication in your SonicWall appliance. Here are some screenshots of my configuration. You will be specifiying the IP address of the device where you installed your DUO Proxy Authentication Software. Please note that you will need to uncheck the Use Radius In check box in the SSL VPN Server Settings section.



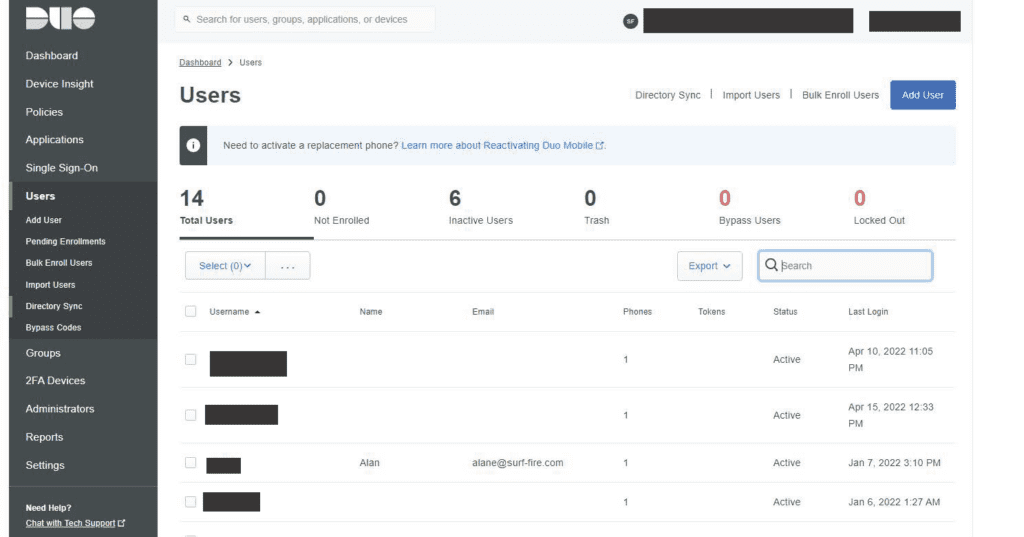
- The last thing you will need to do is setup your users in the DUO website. This included activating their mobile devices for push notification as well. The usernames should match exactly to the username in Active Directory. The domain information will not be passed to DUO so just the username needs to be the same.

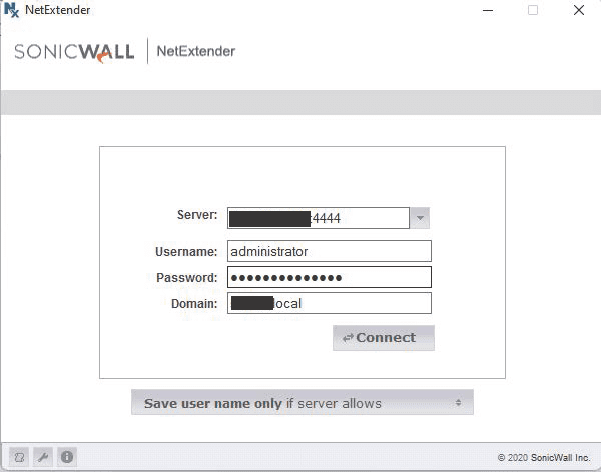
- Now just test your configuration with your SonicWall NetExtender SSL VPN Client and you should get a push verification notice to your mobile device after proper AD user authentication.

Facebook
Twitter
LinkedIn
Reddit
Email
Print
Home » Setup DUO 2FA with SonicWall SSL VPN